NotPetya - Ransomware or NotRansomware?
Whatever you do
Do. NOT. Pay. The. Ransom!
This Tuesday a new wave of cyber attacks hit the world. This new strain of malware, similar to WannaCry, dubbed NotPetya (or officially - ExPetr) by Kaspersky researchers has surfaced in Ukraine. Targeting business infrastructure, NotPetya originally appeared to be a piece of malware, aiming to encrypt important files, demanding a ransom and threating to release them to the public. NotPetya has since spread like wildfire over the world, hitting Russia, Western Europe and North America. As with all other ransomware, paying the NotPetya ransom is pointless, as all you would be doing is funding further criminal activity. Furthermore, researchers have recently come to the conclusion that NotPetya might be a wiper pretending to be ransomware, eliminating the chance of data recovery even if the ransom is paid.
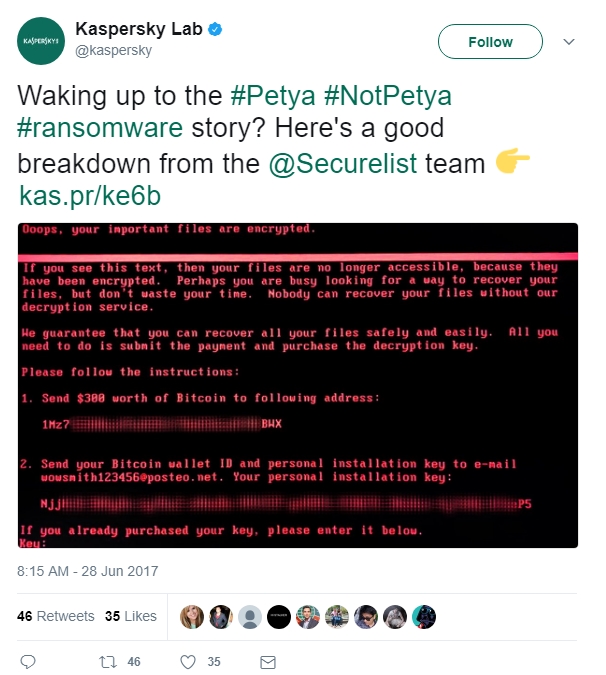
Image Source - Twitter - Kaspersky Lab (@kaspersky)
What is Ransomware?
Ransomware is a type of malware that aims to export money (ransom) from the afflicted victims. Most pieces of ransomware will lock down a computer and its important files, demanding money to undo the damage. Ransomware tends to spread masquerading as an email attachment or a harmless file that you can “download right now and achieve instant results”. Either way, the end result is the same – your important files are encrypted and a certain sum of money is demanded of you.
NotPetya Utilises an Exploit Similar to WannaCry
NotPetya and WannaCry share a common spreading tactic
A recent variety of ransomware, however, used an approach, differing from the standard. The WannaCry worm was capable of travelling between computers on its own, without user interaction. In doing so, it was utilising an exploit under the name of EternalBlue, which Windows XP, Windows Server 2003, Windows Vista, Windows 7, Windows 8, Windows 8.1, and Windows 10 were all vulnerable to. Microsoft had released a fix for the new systems, two months prior to the surfacing of WannaCry, but many companies were not quick to implement the updates and suffered the consequences. On the very next day after WannaCry came about, Microsoft released fixes for the unsupported Windows XP, Windows Server 2003, and Windows 8 as well.
The Fall of WannaCry
The WannaCry kill-switch and NotPetya’s lack thereof
WannaCry was eventually defeated when a researcher discovered its built-in kill-switch. Originally designed to protect the piece of malware from cyber security researchers, the kill-switch was used to render it helpless, ultimately leading to its timely defeat.
What is a Wiper and why Would NotPetya be One?
NotPetya – Ransomware or NotRansomware
Wipers are a type of malware that has seen the most use in the Middle East, targeting large banks and corporations. When they affect a system, they prepare to damage and destroy sensitive files, rendering them unrepairable. Some strains aim to straight up render a system unbootable while others target and destroy specific files over long periods of time, making them hard to detect and combat.
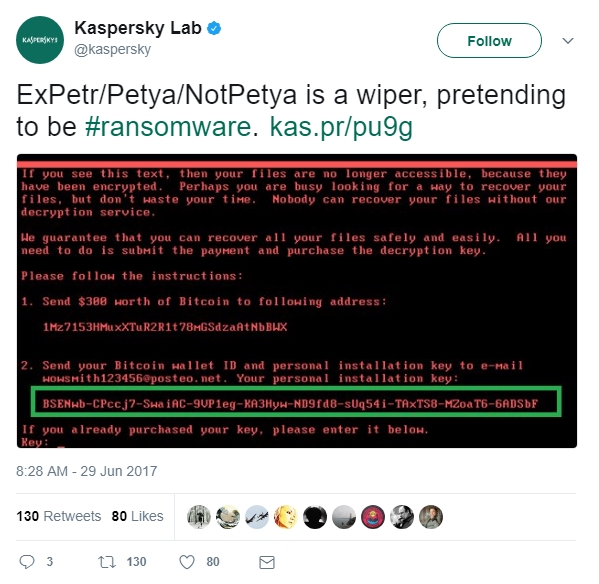
Image Source - Twitter - Kaspersky Lab (@kaspersky)
Why the name NotPetya?
How ExPetr got its unofficial NotPetya name
Originally, the new piece of malware was referenced as merely a version of Petya. As it often happens with social media and hype, the idea that this was indeed a resurfacing of Petya was going to stick. The possible dangers of this were numerous - not only would researchers get side-tracked by this wrong assumption but a multitude of businesses could suffer as a result. Just as the “trend” was getting solidified, Kaspersky researchers stepped in, shining a light on the subject. To eliminate the chance of mistakes, the new strain was dubbed NotPetya and all posts from there on out would reference both of the Petya and NotPetya hashtags.
NotPetya is Significantly Different from the Previously Known Varieties of Petya
Even though similar by name, NotPetya is most certainly a completely new threat
Kaspersky researchers have stated that the new NotPetya malware differs greatly from the previous incarnations of Petya. Furthermore, the idea that NotPetya is either a resurfacing of WannaCry or a variation of Petya have been debunked. And even though NotPetya aims to exploit the same weakness that WannaCry did, researchers seem to be completely certain that it is a whole different animal. On top of that, according to latest data, NotPetya has not been created with financial benefit in mind.
NotPetya or Petya, Do Not Pay the Ransom. Ever.
There is even less of a point to paying the NotPetya ransom than there is with actual ransomware
Whenever your systems are affected by ransomware, paying the ransom is never worth it. Not only do cyber criminals lack regard for the integrity of your company, but they will also use your money to further their unsavoury activities. The best defence against ransomware is having a solid security solution in place, supported by reliable back-ups, ensuring that your data will not be lost in the case of an attack. Furthermore, according to the latest information, NotPetya is not even designed with an unlock feature in mind. Most ransomware feature pieces of code that are capable of unlocking data, should they be provided with the correct decryption key. Seeing as how NotPetya Is lacking this feature, classifying it as a piece of ransomware is no longer logical.
As a London-based cyber security and online business solutions provider, Go Live UK can offer you an immediate, no-obligation consultation on the proper implementations of cyber security. Click here to get in touch with our experts now!
Go to | Benefits of Social Media Marketing That You Can Leverage